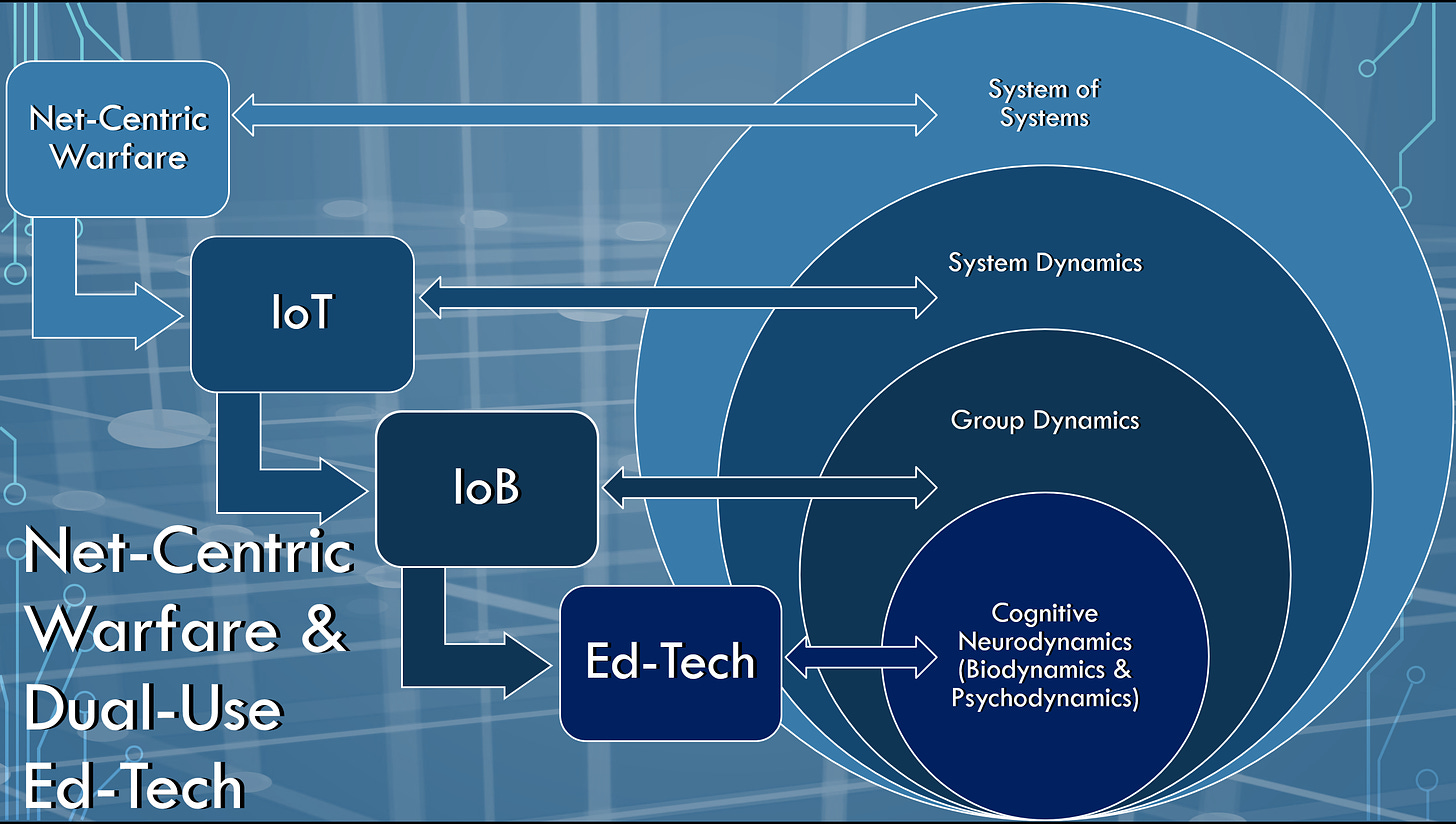
This presentation breaks down how education technologies are being appropriated for dual-use military applications in 4th and 5th Generation Warfare (4GW and 5GW). By data-mining students’ biometrics and psychometrics, dual-use ed-tech compiles individual student psychological profiles that can be aggregated into group gestalts. Through internet-of-bodies (IoB) and internet-of-things (IoT) networks, dual-use ed-tech can be leveraged to socio-emotionally condition group dynamics to conform to the technocratic systems dynamics of the Fourth Industrial Revolution (4IR). Under the pretense of cybersecurity, military and intelligence agencies integrate net-centric “systems of systems” that can backdoor ed-tech cybernetics through the IoB and the IoT in order to generate AI predictive analytics for the command-and-control technocracy of the 4IR.
So this presentation is going to build on the research compiled in my book, which is titled School World Order: The Technocratic Globalization of Corporatized Education [1] . The book covers a progression of evolving technologies, beginning with screen-based technologies, then moving to wearable technologies, then moving to implantable technologies. The screen-based technologies include adaptive-learning courseware; the wearable technologies include socio-emotional (SEL) biofeedback wearables; and the implantable technologies include brain-computer interfaces (BCIs) and eventually nanotechnologies. The latter two types of education technologies, the adaptive-learning courseware and the SEL biofeedback wearables, data-mine students’ cognitive-behavioral algorithms (or, in other words, their thinking algorithms) and their socio-emotional algorithms (or, in other words, their feeling algorithms) respectively. This data is then used to develop artificial intelligence (AI) systems, which is primed to interface with human nervous systems through BCIs. These AI systems can also be used to build social credit databases and predictive analytics, which can be used for 4GW and 5GW net-centric warfare in the globalist command-and-control technocracy of the 4IR.
As a segue, as we dive into the military applications of dual-use ed-tech, we can start by looking at some of the earliest intelligent tutoring [2] systems that were developed [3] by the US Navy [4] , and also some of the earliest iterations of the analog precursors to the modern digital adaptive-learning courseware were developed [5] with help from the US Navy, the US Airforce, and the Human Resources Research Organization (HumRRO), which is a division of the United States Army.
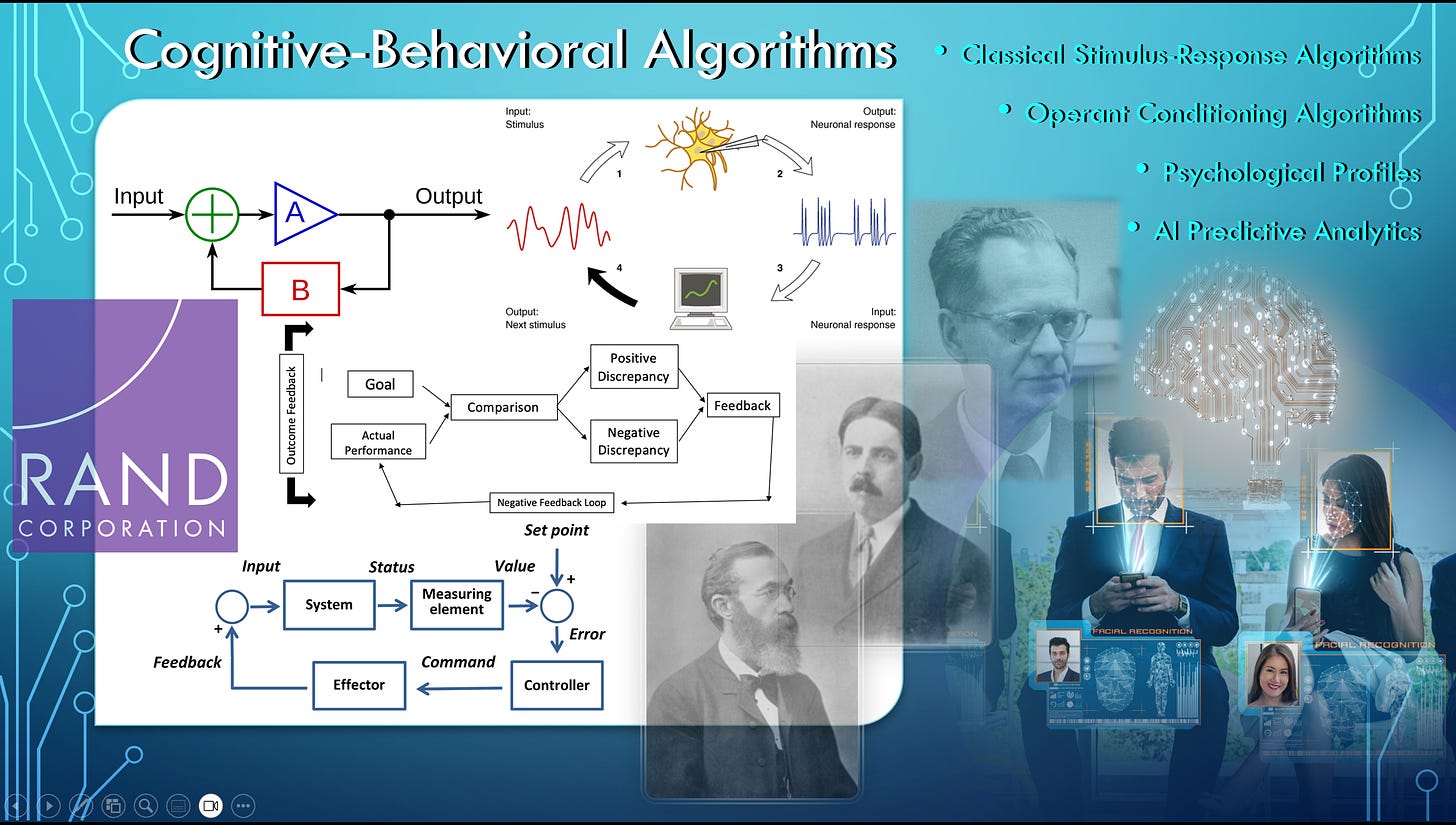
The cybernetic basis of intelligent tutoring systems and adaptive-learning AI is built on the cognitive-behavioral psychometrics [6] that come from the stimulus-response [7] feedback loops that were programmed into B. F. Skinner’s operant-conditioning teaching machines [8] . Skinner-box teaching machines augmented the classical stimulus-response conditioning that was formulated by Wilhelm Wundt and then refined into behaviorism by psychologists like E. L. Thorndike; and then eventually Skinner came along and was able to program behaviorist stimulus-response loops into algorithms that could be automated through his analogue teaching machines, which have evolved into modern digital adaptive-learning courseware. Built in to these stimulus-response loops are basically the feedback loops that are the bedrock that enable artificial intelligence to track progress and predict outcomes for individual students, groups of students, and whole schools.
If you look at the data inputs and outputs on a computer, these are basically corollaries [9] to the stimulus and response respectively: the stimulus being the environmental input and the response being the behavioral output. These environmental-input/behavioral-output feedback loops [10] can be used to map out scenario planning, programming, and budgeting systems [11] developed by the RAND Corporation for central planning of the broader economy [12] encompassing outcomes-based education [13] in a 4IR [14] command-and-control economy [15] .
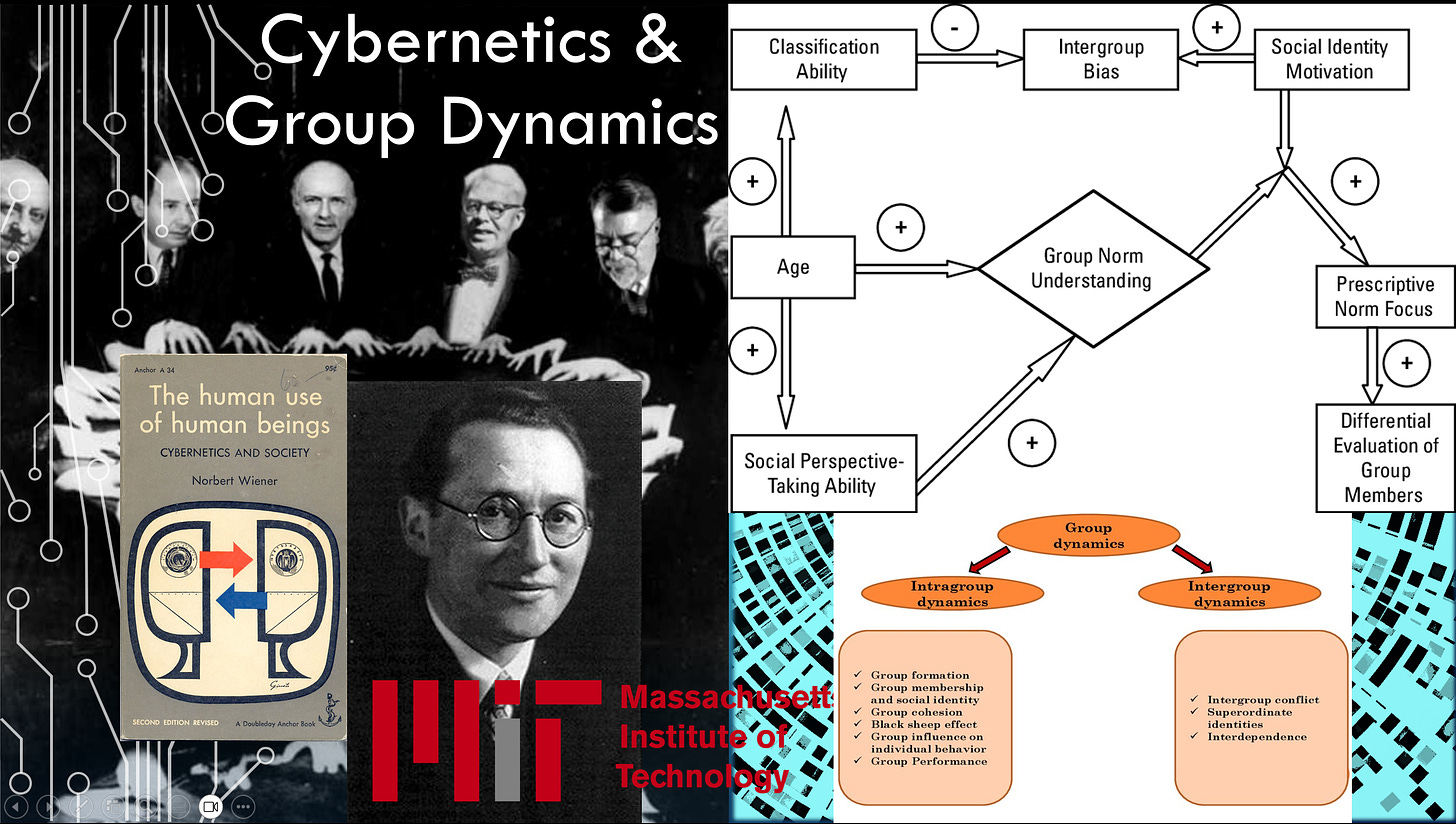
The architecture for the feedback loop was put together at the Macy Cybernetics Conferences [16] during the late 1940s and early 1950s by people like Norbert Wiener, who wrote The Human Use of Human Beings: Cybernetics and Society [17] . It was at the Macy Cybernetics Conferences [18] that the subliminal and conditioned reflexes of human consciousness were mathematically reduced to neurochemical stimulus-response loops that mirror the electrical input-output loops of a binary-coded digital computer.
This can be done at an individual scale, but it can also be done at a group scale. Another attendee at the Macy Cybernetics Conferences was Kurt Lewin [19] , who came up with “Group Dynamics” [20] because he believed that individual stimulus-response conditioning is most effective when reinforced with the social punishments and rewards of group dynamics. So he developed the Center for Group Dynamics at the Massachusetts Institute of Technology (MIT).
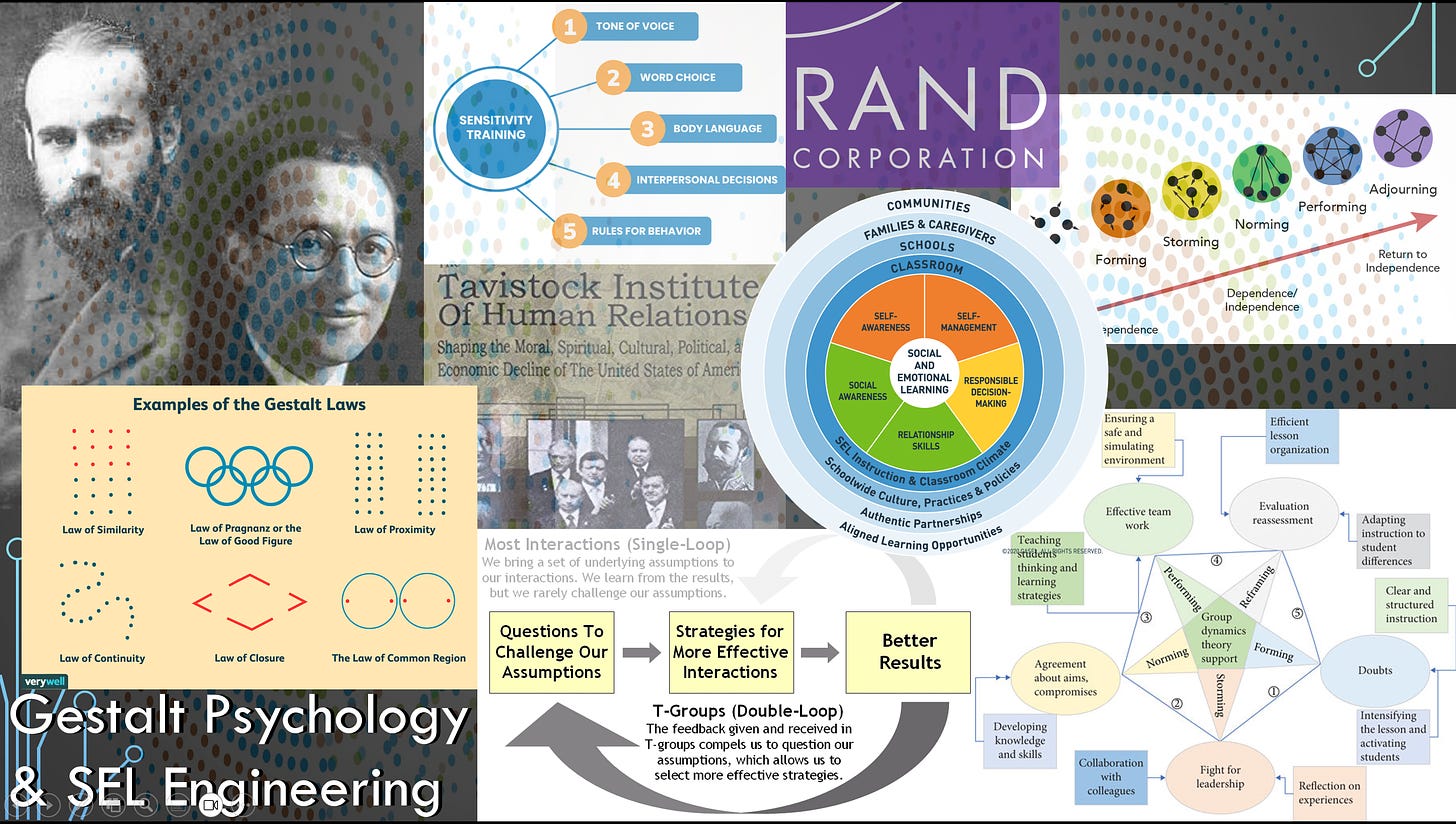
He worked with Max Wertheimer [21] , who was one of the founding fathers of gestalt psychology [22] . Lewin harnessed gestalt psychology to socio-emotionally engineer politically correct group dynamics. He was influential in the founding of the Tavistock Institute of Human Relations [23] , which facilitated [24] “T Groups,” [25] which were also created by Lewin. These T Groups correlate [26] with another one of his projects known as “sensitivity training” [27] . Through T Groups and sensitivity training, individuals can be conditioned to conform to group gestalts.
In the realm of education, a pedagogy known as “socio-emotional learning” (SEL) [28] advances ed-tech methodologies that incorporate biofeedback wearables. With the aid of SEL biofeedback wearables, which data-mine students’ emotional algorithms through EEGs [29] , EKGs [30] , and GSR [31] (in other words brainwaves, heart rates, and galvanic skin response), students can be conditioned to conform to the group gestalts of classroom groups, school groups, and the broader community at large.
By shuffling intergroup and intragroup dynamics through T Groups and sensitivity training, SEL biofeedback conditioning can be leveraged to shape and reshape group gestalts to conform to the technocratic systems dynamics of the 4IR. It’s worth noting here that the RAND Corporation [32] has collaborated with the Fetzer Institute [33] , which set up the Collaborative for Academic, Social, and Emotional Learning (CASEL) [34] . CASEL is one of the main clearinghouses for socioemotional-learning initiatives in the United States.
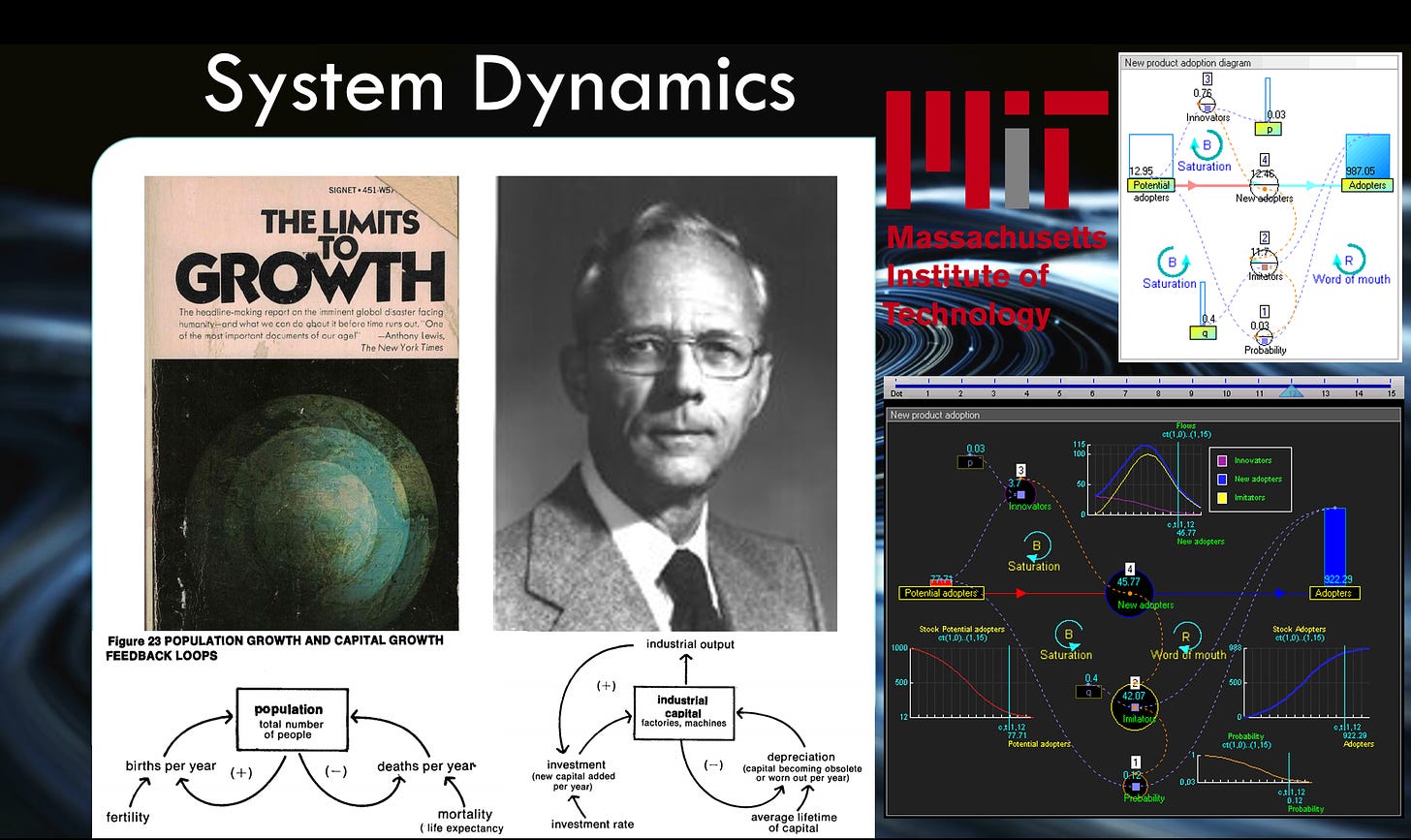
What are systems dynamics? Systems dynamics [35] are computational models that graph complex, non-linear superstructures that encompass institutional political-economic relations. So these could be supply-chain dynamics [36] , population growth dynamics [37] , public healthcare dynamics [38] , school system dynamics [39] , just to give you a few examples.
The concept of systems dynamics was developed by Jay W. Forrester [40] . As an MIT professor, he formulated the theory of systems dynamics while studying supply-chain dynamics at General Electric. He was also one of the architects of the Club of Rome’s Limits to Growth [41] document, which graphed population growth and environmental resource consumption models for the systems dynamics of what is now known as sustainable development [42] in the 4IR Great Reset.
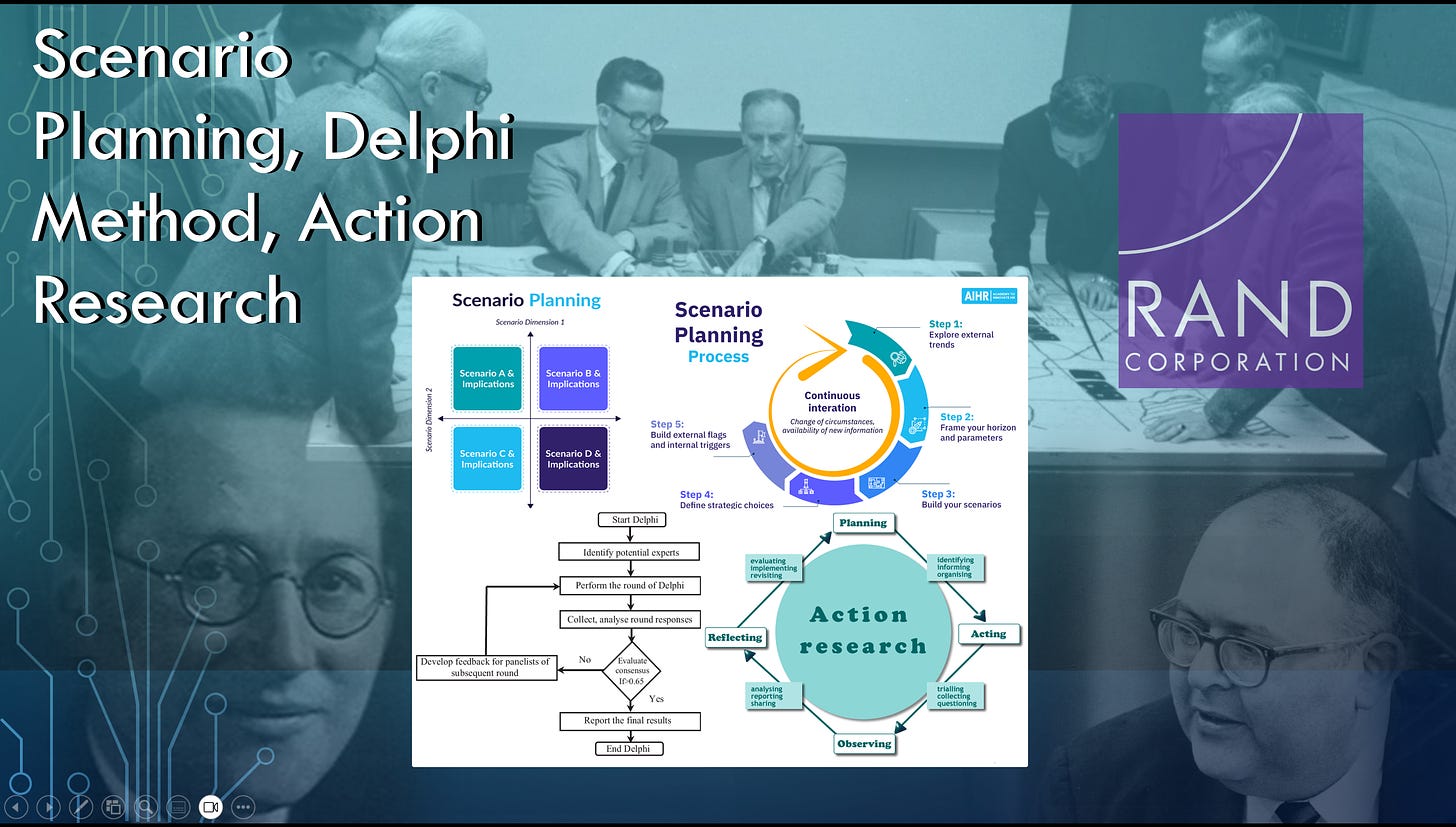
4IR systems dynamics can be advanced through a combination of scenario planning, which was developed by Herman Kahn [43] , who was an official at the RAND Corporation [44] ; the Delphi method [45] , which was developed [46] by Olaf Helmer [47] , who was another RAND Corporation [48] official; and action research [49] , which was developed Kurt Lewin. Scenario planning is basically a non-linear augmentation [50] of Planning, Programming, and Budgeting Systems (PPBS); the Delphi method garners artificial consensus creation through group dynamic conditioning [51] ; and action research is essentially a method of monitoring and adjusting scenario plans and other PPBS plans through feedback loops [52] .
To synthesize all that, the Delphi method primes populations to desire and pursue the gamified scenario plans for the 4IR while action research feedback loops enable technocrats to track, trace, and adjust progress toward their ideal scenario plan for the 4IR. Through this feedback-loop infrastructure, technocrats can pivot from conditioning the individual to conditioning the group, in turn conditioning the group conform to the broader systems dynamics of the planned economy of the 4IR.
Enter “system of systems,” [53] which was developed by William A. Owens [54] . Another affiliate with the RAND Corporation, Owens is the architect of “revolution in military affairs” (RMA) [55] , out of which 4GW [56] and 5GW were spun. One of the key components of 4GW is the involvement of “non-state actors” in military affairs (in other words, involving civilians in the pursuit of military goals).
Integral to system of systems is “network-centric,” [57] or “net-centric,” warfare, which is basically a cybernetic exploitation of systems dynamics and group dynamics through a ubiquitous track-and-trace system that enables what is known as “full-spectrum dominance” [58] by the United States military. Full-spectrum dominance involves the dominance of five domains: land, sea, air, outer space, and information cyberspace.
Through net-centric system-of-systems dominance, technocrats can put together predictive anti-terror [59] and precrime analytics [60] , which could be exploited to flag politically incorrect psychometrics as an impetus to pre-empt undesirable scenarios. At the same time, technocrats can also use command-and-control cybernetics to prime the minds of individuals and groups, including non-state actors, with psychological operations [61] that nudge behaviors toward globalist 4IR scenarios. In brief, through system of systems, technocrats can wield the net-centric data feedback necessary to steer scenario planning, the Delphi method, and action research in ways that condition individuals to conform to groups while simultaneously conditioning groups to conform to the broader systems dynamics of the 4IR.
So, what are some solutions? What can we do about this other than be aware of the realities of it and therefore be able to anticipate the ways that we are being gamified through the system of systems. A few practical solutions involve trying to thwart their ability to garner signals from their analytics.
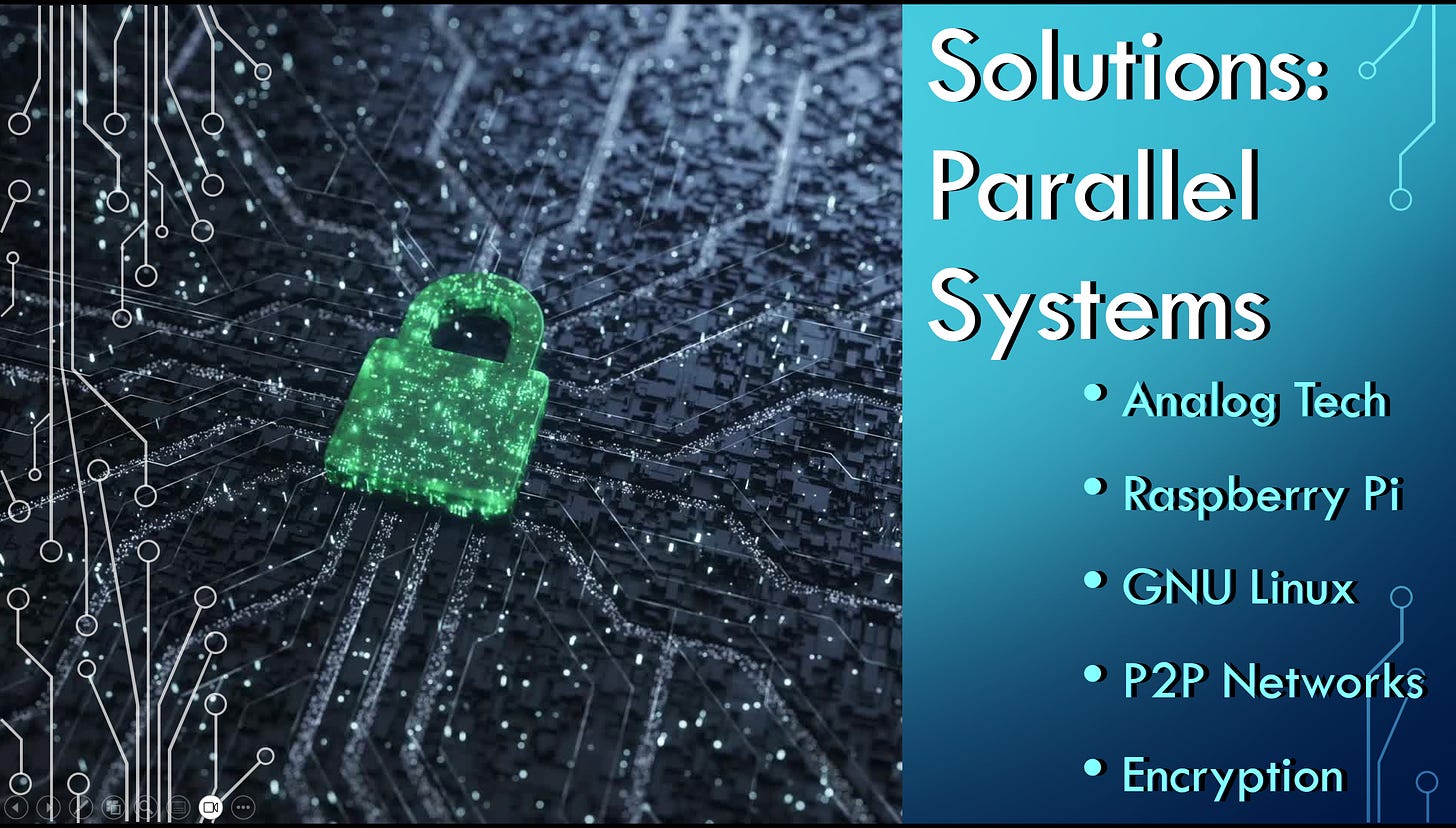
Perhaps the most effective option we could start with would be going as off-grid as possible, which entails using as much analog tech as possible. But, for the world that we live in, that’s probably not entirely possible for everyone. So there are various ways we can use different types of technologies that can bypass cybernetic tracking systems.
We can start with alternative hardware, like Raspberry Pis, which could bypass firmware backdoors that are installed in the hardware chips on Big Tech devices. Concerning alternative operating systems, we can use GNU Linux systems, which could skirt Big Tech data-mining, such as AI data-mining from the Microsoft Co-Pilot Recall [62] that is being installed in new Windows 11 operating systems. We can also build alternative peer-to-peer networks that can bypass ISP tracking. Then, insofar as we might opt to using any of technologies that do not fall under this umbrella of alternative tech, it’s important to use encrypted software and encrypted communications as much as possible, and even carry a Farraday cage to block geolocation when you’re moving around in physical space.
So these are just a few practical ways that we can reduce the abilities of these various technocratic systems to data-mine us for predictive analytics and to gamify our behaviors.
Thank you.
https://www.trineday.com/products/school-world-order?_pos=1&_psq=school&_ss=e&_v=1.0 ⮥
https://onlinelibrary.wiley.com/doi/10.1111/j.1756-8765.2010.01098.x ⮥
https://stemeducationjournal.springeropen.com/articles/10.1186/s40594-018-0110-y ⮥
https://www.nre.navy.mil/media-center/news-releases/onr-developing-digital-tutors-future-naval-scientists-engineers ⮥
https://unlimitedhangout.com/2021/09/investigative-reports/nea-world-order/ ⮥
https://www.globalresearch.ca/cognitive-behavioral-workforce-conditioning-through-online-adaptive-learning-technetronics/5639003 ⮥
https://dissidentvoice.org/2017/09/secretary-devos-neurocore-and-competency-based-workforce-training/ ⮥
https://rense.com/general96/virtual-school-in-a-computerized-box.html ⮥
https://openknowledge.worldbank.org/server/api/core/bitstreams/edf064f0-d5c9-58a2-bdd2-06501f286132/content ⮥
https://archive.org/details/DeliberateDumbingDownOfAmerica_201404/mode/2up?q=ppbs ⮥
https://www.weforum.org/agenda/2018/06/construction-industry-future-scenarios-labour-technology/ ⮥
https://press.uchicago.edu/ucp/books/book/distributed/C/bo23348570.html ⮥
https://direct.mit.edu/books/oa-monograph/4664/The-Cybernetics-Group ⮥
https://archive.org/details/maxwertheimerges0000king/mode/2up?q=lewin ⮥
https://link.springer.com/referenceworkentry/10.1007/978-3-030-38324-4_13 ⮥
https://www.researchgate.net/publication/238400476_Kurt_lewin_at_the_tavistock_institute ⮥
https://www.newyorker.com/culture/cultural-comment/the-radical-history-of-corporate-sensitivity-training ⮥
https://www.activistpost.com/2020/02/socioemotional-thought-crimes-in-american-schools-tracking-student-sel-data-for-precrime.html ⮥
https://www.activistpost.com/2020/12/a-brave-school-world-of-tracking-student-data-for-social-credit.html ⮥
https://unlimitedhangout.com/2022/05/investigative-reports/barbara-marx-hubbard-godmother-of-transhumanism-and-synthetic-spirituality/ ⮥
https://nepc.colorado.edu/blog/gates-foundation-explains-galvanic-skin-response-monitor-plus ⮥
https://www.rand.org/pubs/external_publications/EP19990029.html ⮥
https://www.edutopia.org/social-emotional-learning-history ⮥
https://www.sciencedirect.com/science/article/abs/pii/S0959652618331147 ⮥
https://www.sciencedirect.com/science/article/pii/S1877050920304208 ⮥
https://news.mit.edu/2016/professor-emeritus-jay-forrester-digital-computing-system-dynamics-pioneer-dies-1119 ⮥
https://archive.org/details/TheLimitsToGrowth/page/n11/mode/2up?q=forrester ⮥
https://www.amazon.com/Great-Reset-Struggle-Liberty-Unraveling-ebook/dp/B0BLJ2P25H ⮥
https://www.sciencedirect.com/science/article/abs/pii/S0016328712001978 ⮥
https://archive.org/details/predictingfuture0000resc/mode/2up?q=helmer ⮥
https://www.tandfonline.com/doi/pdf/10.1080/0965079930010102 ⮥
https://www2.deloitte.com/content/dam/Deloitte/us/Documents/public-sector/ppbe.pdf ⮥
https://www.academia.edu/399894/The_Delphi_Method_As_a_Research_Tool_An_Example_Design_Considerations_and_Applications ⮥
https://www.rand.org/content/dam/rand/pubs/research_reports/RR1700/RR1708/RAND_RR1708.pdf ⮥
https://www.rand.org/content/dam/rand/pubs/documented_briefings/2005/RAND_DB311.pdf ⮥
https://web.archive.org/web/20161224220150/http:/www.dtic.mil/jv2010/jv2010.pdf ⮥
https://www.chathamhouse.org/sites/default/files/2019-08-07-AICounterterrorism.pdf ⮥
https://www.rand.org/content/dam/rand/pubs/monograph_reports/MR1016/RAND_MR1016.pdf ⮥
https://arstechnica.com/gadgets/2024/05/microsofts-new-recall-feature-will-record-everything-you-do-on-your-pc/ ⮥





















Net-Centric Warfare and Dual-Use Ed-Tech by John Klyczek | Chișinău Forum 2024